Securing the Game: The Role of Penetration Testing in the Gaming Industry

The gaming industry has experienced exponential growth over the past decade, transforming from simple arcade games into complex, interactive, and highly immersive experiences. With the rise of online multiplayer games, virtual economies, and e-sports, the stakes have never been higher. However, with great popularity comes great risk. Cybersecurity threats are a significant concern for game developers and players alike. This is where penetration testing comes into play.
Why Cybersecurity Matters in Gaming
Online games often require personal information from players, including email addresses, payment details, and sometimes even more sensitive data. Additionally, virtual economies in games like "World of Warcraft" or "Fortnite" mean real-world money is at stake. Hackers target these games to steal personal information, disrupt services, and exploit game mechanics for unfair advantages.
Understanding Penetration Testing
Penetration testing, or pentesting, is a proactive approach to identifying security vulnerabilities in a system before malicious hackers can exploit them. It involves simulating cyberattacks on a system to uncover weaknesses that could be exploited in a real attack.
The Role of Pentesting in the Gaming Industry
- Protecting Player Data: One of the primary concerns in gaming is the protection of player data. Pentesting helps ensure that personal information and payment details are securely handled and stored, reducing the risk of data breaches.
- Ensuring Fair Play: Cheating and exploiting game mechanics can ruin the gaming experience for honest players. Pentesting can identify and mitigate vulnerabilities that allow such exploits, maintaining a fair and enjoyable environment for all players.
- Securing Virtual Economies: Many games feature virtual economies where in-game items and currency have real-world value. Pentesting helps protect these economies from fraud and theft, preserving the integrity of the game and the trust of the players.
- Preventing Service Disruptions: Distributed Denial of Service (DDoS) attacks can take game servers offline, leading to frustrated players and lost revenue. Pentesting can help identify and fortify against such attacks, ensuring continuous service availability.
Common Vulnerabilities in Gaming
- SQL Injection: Attackers can manipulate game databases through malicious SQL queries, accessing or altering data.
- DDoS Attacks: Distributed Denial of Service (DDoS) attacks can overwhelm game servers, causing downtime and a poor experience for players.
- Cross-Site Scripting (XSS): Hackers can inject malicious scripts into game websites, affecting players who visit the site.
- Server-Side Vulnerabilities: Weaknesses in-game servers can be exploited to gain unauthorized access or disrupt services.
- Client-Side Vulnerabilities: Flaws in game clients can allow attackers to cheat or exploit the game.
- Data Breaches: Online gaming platforms house vast quantities of sensitive user data, including personal details, payment information, and gaming preferences. This makes them prime targets for cybercriminals. Such breaches can result in identity theft, financial fraud, and significant damage to the reputation of gaming companies, eroding trust among players and stakeholders.
Notable Data Breaches in Gaming
Insomniac Games (2023): At the end of 2023, Insomniac Games, a subsidiary of Sony, fell victim to the ransomware gang Rhysida. The group initially demanded a ransom of $2 million USD, later leaking 1.3 million files on the dark web after failing to find a buyer. Rhysida uploaded 1.67 TB of data in three parts. The leaked materials included design documents, casting information, level designs for the Wolverine game, internal communications, HR documents, and non-disclosure agreements with major companies.
Epic Games (2019): In January 2019, a significant security vulnerability in Fortnite, the popular online game with over 200 million users, was exposed by security research firm Check Point. Hackers exploited an old sub-domain, 'http://ut2004stats.epicgames.com', created by Epic Games in 2004 for another game, Unreal Tournament, to send phishing links to Fortnite users, appearing as legitimate communication from Epic Games. Clicking these links allowed hackers to hijack accounts without needing login information, enabling them to make unauthorized purchases and secretly record in-game conversations.
Check Point's research revealed a sophisticated method involving SQL injection and cross-site scripting (XSS) attacks. Hackers manipulated the "redirectedUrl" parameter in the SSO (Single Sign-On) mechanism to direct users to a malicious sub-domain containing the XSS payload. This allowed them to capture the OAuth token and gain unauthorized access to user accounts.
Epic Games quickly addressed the issue once alerted by Check Point, taking down the compromised webpage and advising players to use strong, unique passwords and avoid sharing account information. This incident, along with a previous security issue found by Google researchers in August 2018, underscores the growing risk of cyber-attacks targeting Fortnite due to its immense popularity and profitability, with the game projected to make $3 billion in profit by the end of 2018.
Activision (2022): Activision, a video game developer most famous for creating Call of Duty and World of Warcraft, experienced a social engineering attack and a data breach in 2022. Hackers successfully phished an Activision employee, gaining access to the internal network and game data. Activision only recently confirmed the breach. The stolen data included names, phone numbers, job titles, locations, and email addresses of 19,444 employees, which were posted on the Breached hacking forum. Activision initially claimed that no sensitive data was accessed and that the incident was swiftly resolved, with no compromise to game source code or player data. However, the appearance of this data on a popular hacking forum raises significant risks for phishing and social engineering attacks against Activision employees.
Example of phishing SMS messages that were sent to employees:
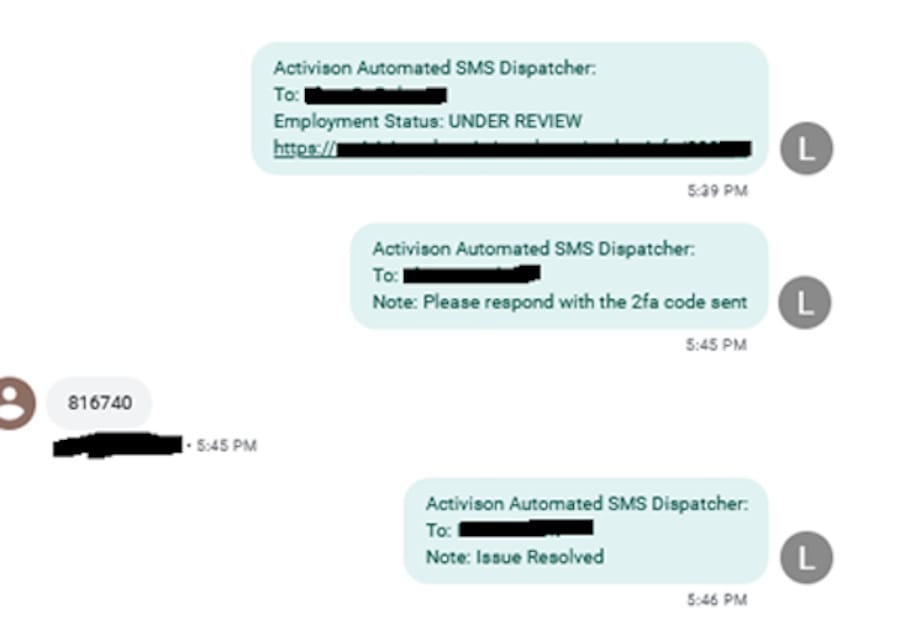
EA (2021): In June 2021, Electronic Arts (EA) experienced a significant data breach in which hackers stole over 780 GB of data, including the source code for several company IPs. Hackers breached the company by purchasing stolen cookies for $10, which they used to access EA's Slack channel. Once inside, the hackers messaged EA's IT support, claiming they lost their phone at a party and requested a multifactor authentication token. The hackers successfully obtained the token twice, granting them access to EA's corporate network.
Inside the network, the hackers located a service used by EA developers for compiling games. They created a virtual machine to gain further visibility and subsequently downloaded the game's source code. EA confirmed the breach, stating that a limited amount of game source code and related tools were stolen, but no player data was accessed. The stolen documents included materials on PlayStation VR, FIFA game digital crowds, and AI in games.
Despite a ransom demand, EA chose not to comply, resulting in the data being leaked online for illegal access and download. Fortunately, no private player data was compromised in the breach.
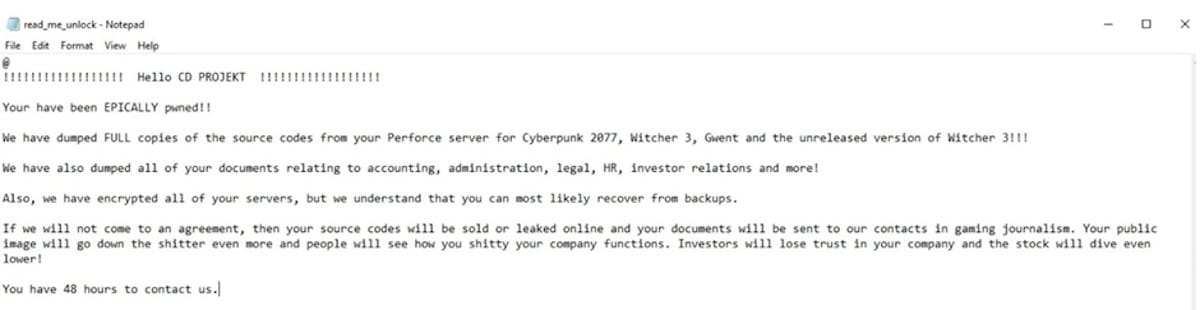
CD Projekt Red (2021): The developers of the popular games "Cyberpunk 2077" and "The Witcher 3" were victims of a ransomware attack. Hackers stole source code for several games and internal documents, which were later auctioned off on the dark web. They reportedly received $7 million in return.
The message the CD Projekt Red team received after their data was encrypted:
Nintendo (2020): In 2020, Nintendo experienced a significant security breach, also known as the Nintendo Gigaleak. The leaks started in March 2018 but became prominent in July 2020 when large amounts of sensitive data, including game and console source codes, development tools, and internal documentation, were released on the anonymous imageboard 4chan. These leaks originated from companies contracted by Nintendo and individuals previously convicted of hacking Nintendo's systems. The leaked materials included early prototypes, unused assets, and detailed information on various Nintendo consoles and games, including the Super Nintendo Entertainment System, Nintendo 64, and Pokémon series.
The Gigaleak exposed not only Nintendo's proprietary information but also private communications and developers' personal files, raising significant privacy and security concerns. Despite Nintendo's efforts to enhance its security measures following the breach, the incident highlighted the vulnerabilities in its data protection strategies and underscored the ongoing challenges large corporations face in safeguarding sensitive information.
Capcom (2020): In November 2020, Capcom, the developer behind Resident Evil, Monster Hunter, and Street Fighter, suffered a severe security breach. The attackers demanded a ransom of $11 million to decrypt the data and prevent its public release. Capcom chose not to pay the ransom, leading to the leak of the stolen personal data, including players' names, addresses, phone numbers, and email addresses.
Capcom now estimates that up to 390,000 people might have been affected by the breach, adding 58,000 individuals to the list since the previous update while removing 18,000 from the North American Capcom Store and eSports operations website. Initial reports confirmed the compromise of sales and financial information and the personal details of nine employees. However, up to 350,000 records, including addresses, phone numbers, and email addresses, might have been compromised, though credit card information was not included.
How ONSEC.io Can Help
At ONSEC.io, we specialize in pentesting services tailored to the unique needs of the gaming industry. Our team of experts understands game developers' specific threats and challenges. We provide comprehensive security assessments, combining manual and automated testing methods to uncover and address vulnerabilities effectively.
Conclusion
In the fast-paced and competitive world of gaming, cybersecurity is not just an option; it's a necessity. Pentesting plays a crucial role in protecting player data, ensuring fair play, securing virtual economies, and preventing service disruptions. By partnering with ONSEC.io, you can safeguard your game and provide a secure, enjoyable experience for your players.
Contact ONSEC.io team at [email protected] or leave a request for consultation on our website www.onsec.io today to learn more about our pentesting services and how we can help protect your game from cyber threats.