Lock'n'load. History of vulnerabilities in the Counter Strike series - Part 1

Buffer Overflow
Introduction
Since this article will largely focus on the topic of buffer overflow, let's dive into this topic.
Buffer Overflow is one of the most well-known and widely exploited vulnerabilities in cybersecurity. This vulnerability allows attackers to overwrite data in a program's memory and potentially - execute arbitrary code, and gain control over the system.
So, what is a buffer?
A buffer is a portion of memory allocated for temporary data storage. A buffer overflow occurs when a program is given more data than the buffer can hold. As a result, the excess data overwrites adjacent memory locations, which can lead to unexpected and undesirable consequences.
Let's look at how memory works in the C programming language.
Assume we are using a 64-bit Linux system, the gcc compiler, and we want to create a variable that stores 16 text characters.
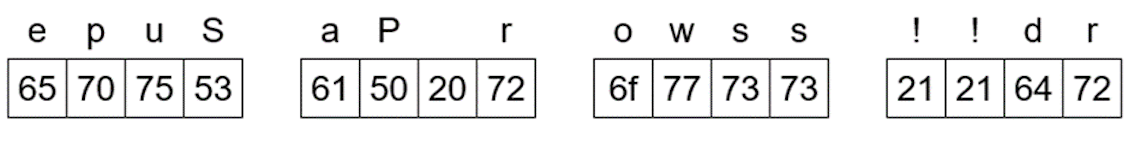
Let's imagine how the string "Super Password!!" looks like in memory.
First, each character is represented by its HEX value from the UTF-8 table.
Thus, the character S will have HEX - 53, u - 75, p - 70, and so on.
Then the numbers are stored in Little Endian order, meaning they are divided into 4 bytes and written from the least significant byte to the most significant byte.
Here is an example of how the string "Super Password!!" would look like in memory:
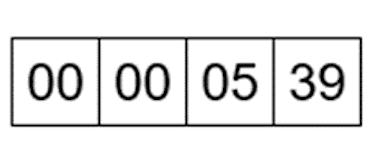
The situation is similar to the Integer type. In C, under these conditions, an int occupies 4 bytes. Let's see what the number 1337 looks like in memory.
First, we'll convert it to HEX: 1337 -> 539, then add the necessary 0 and write it in Little Endian format:
Practice
Now that we have some understanding of how variables are stored let's move on to an example.
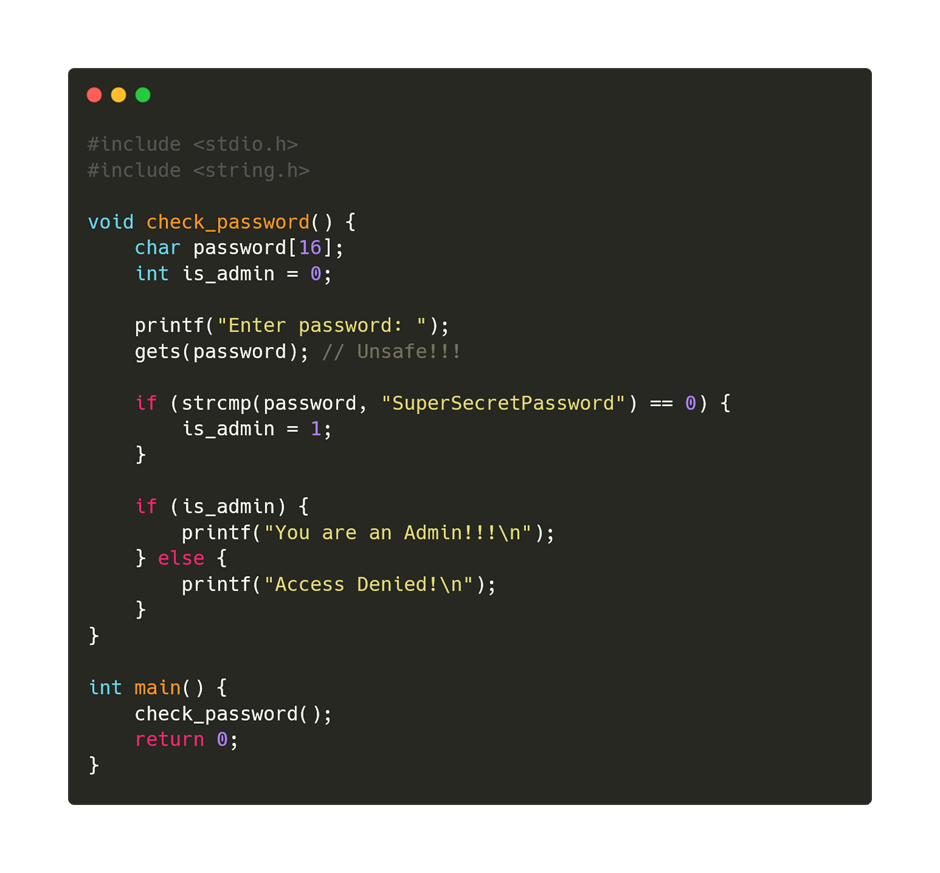
First, let's create a small program with the following functionality:
1) The program reads the user's password
2) The program checks the password by comparing it with the correct one
3) If the password is correct, it sets the flag is_admin = 1
4) If is_admin = 1, it grants administrator rights
Here is the full code of the program:
Let's run our program through the gdb debugger and look at the state of the stack after initializing the variables:
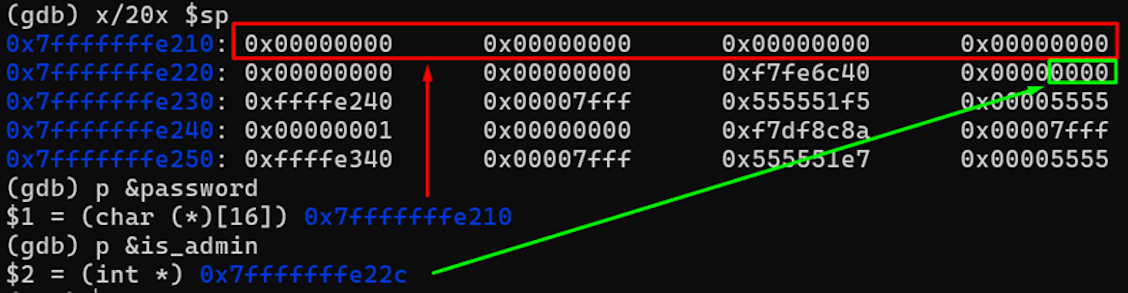
The screenshot shows that the first 16 bytes (4 by 4 bytes) are occupied by the array for the input password, then 8 empty bytes, followed by 4 bytes with unknown information, and finally, the field for the is_admin variable.
Let's try running the program and entering a random password:
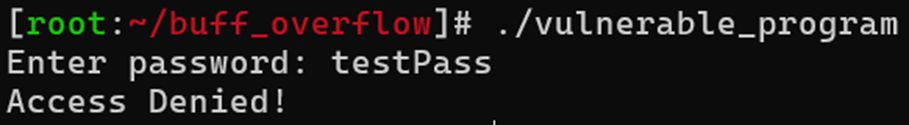
As expected, access is denied.
However, the vulnerable gets function does not check the size of the input data, and the is_admin variable is stored 12 bytes further down the stack.
Let's try to overwrite this variable. For this, we need to write: 16 bytes - password, 2 times 4 bytes - unused memory, 4 bytes - unknown field, 2 bytes - the required Integer.
In total, 16 + 4 + 4 + 4 + 2 = 30 bytes.
Since the check uses the construct if (is_admin), if the value of the is_admin variable is non-zero, the condition is considered true, and the code block inside the if is executed.
This means that we can write anything except zero.
The final string with the exploit will look like this: AAAAAAAAAAAAAAAABBBBCCCCDDDDEE
Let's run the program and check the exploit:
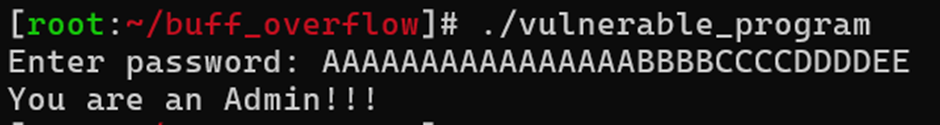
Using gdb, let's check what is happening on the stack at this moment:
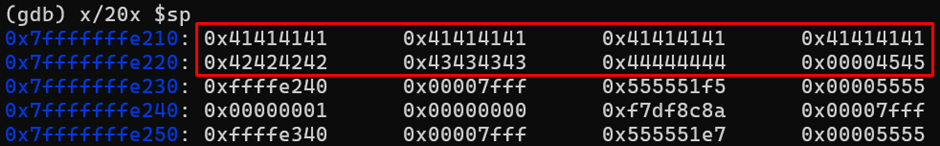
As a result, we overwrote the value of is_admin, thereby bypassing the password check function.
Disclaimer
Despite significant improvements in software security and the introduction of numerous checks, buffer overflow remains one of the most dangerous and relevant vulnerabilities. Modern compilers and operating systems provide various protection mechanisms, such as stack canaries, Data Execution Prevention (DEP), Address Space Layout Randomization (ASLR), and the use of safe functions for string handling, like strncpy instead of the unsafe gets.
However, even with these protective measures, implementation errors in programs can still lead to buffer overflow vulnerabilities. For example, improperly configured security parameters or vulnerabilities in third-party libraries can become entry points for attackers. One example is the Heartbleed vulnerability in the OpenSSL library, which allowed attackers to read data from the server's memory, potentially leading to the leakage of confidential information.
I hope this section has helped deepen your understanding of the basics and dangers of buffer overflow.
Author: @mk1337
To enhance your company's security level, contact ONSEC.io team
Mail us at [email protected],
leave a request for a free consultation
or visit our website www.onsec.io
to learn more about our pentesting services and how we can help protect your game from cyber threats.